In my previous article, I wanted to show people what SASE is, what SASE is NOT, what ZTNA 2.0 means, and how this architecture and mindset can benefit your organization. Here, I want to take things to the next step and discuss the common pain points that lead customers towards a SASE solution as well as help answer any key questions that may lead to a network/security/WAN transformation.
In my previous article, I wanted to show people what SASE is, what SASE is NOT, what ZTNA 2.0 means, and how this architecture and mindset can benefit your organization. Here, I want to take things to the next step and discuss the common pain points that lead customers towards a SASE solution as well as help answer any key questions that may lead to a network/security/WAN transformation.
Finally, I wanted to remind anyone reading this article: The SASE help you need is here! Now, let’s dive in.
Customer Pain Points? Enter SASE!
Many enterprise networking environments today have legacy networking and security production environments, consisting of various point products (many of which are managed separately and do not correlate data together as a platform), mostly due to budget constraints and organic growth over time, with users and perimeters everywhere.
There are also greenfield, hybrid greenfield, and brownfield environments that need guidance and a solid framework to navigate today’s growing security concerns and threat landscape.
WEI Workshop: How SASE Will Transform Your Network & Security
Remember, we have an ever-expanding attack surface, an ever-expanding company perimeter (this includes every user and application), most employees are off site, and most of your data is off site and in the cloud/SaaS applications. Each of these factors produce data leaks, which results in one giant perfect storm when trying to secure data!
Today, there are many security and WAN/network transformation issues which companies are faced with, including:
- ZTNA (Zero Trust Network Access): You might have many security point products (firewalls, URL filtering appliances, IDS/IPS appliances, etc.) and wonder if these products in your environment are built upon the 5 pillars of ZTNA (least privilege access, continuous trust verification, continuous security inspection, protection of all data, and protection of all applications). According to Gartner, a viable SASE product ought to be architected and built upon the 5 pillars of ZTNA.
- Costs: Rising year-over-year costs for networking and security infrastructure, which only increases when you have to maintain many security appliance point products. This includes firewalls, outdated URL filtering appliances, explicit proxy appliances or services, WAN edge routers, an IDS/IPS appliance, a CASB (cloud access security broker), an RBI service (remote browser isolation/enterprise web browsing)...the list is endless. Admins need to upgrade these items, maintain patching, power, and cooling for appliances. Each device or service has its own licensing, configuration console, etc. These devices can be considered legacy, possibly missing the mark on security needs. Replace them…start the process today and downsize the number of manufacturers in your environment!
- Breaches: The looming fear of breaches/security events, issues affecting your environment, and not knowing if the products in your environment are secure or even industry compliant. Do you have the best practice security recommendations configured? Do you have a product that prevents known and zero day (unknown) malware?
- Client VPN
- Having the need to replace legacy insecure client VPN solution(s): Legacy VPN solutions likely only have the ability to “allow [mobile user traffic, whatever that is and where it is destined to], then ignores” user traffic such that, once connected, the user can access anything in the enterprise networking environment. Further, these mobile users are not verified by technologies such as two-factor or machine authentication. Authenticating the actual desktop that the user is using to connect to your environment ensures that this device is a company certified asset prior to user authentication. What to do if the user has a BYOD device that is connecting to your environment? How do you posture check this device, how do you ensure that certain internal user groups only have access to certain applications (and not others) while other internal user groups only have access to other applications? What to do if the user is an outside contractor requiring limited access to targeted applications to only perform certain specific functions?
- Infected Desktops: What happens if a VPN user connects to a corporate environment with an infected or non-compliant machine? What happens if VPN user’s desktop becomes infected while connected to the corporate environment?
- Solid User Experience: Most client VPN connections in today’s enterprise network environments are backhauled to one HQ or data center site to a firewall. The data is processed from that egress point out to the Internet or to a remote branch. What happens if the user is in California then VPNs back to a data center in New York, only to then have the data go to a website in San Francisco? Or worse, what if the users are not in the U.S. but need to VPN back to one site in the U.S. just so that security can be applied? So, when a user connects to your corporate environment via client VPN, how do you mitigate adverse factors to ensure a solid user experience without latency, jitter, or delay? Because of this, admins opt to use “split tunneling” to improve mobile user experience. This way, the mobile user traffic can route back to a corporate office when needed, but go to the Internet via the mobile user’s home Internet connection. Problem solved, right? Not so fast! Now, the admin can no longer secure the mobile user’s Internet traffic (or at least making this more difficult, prompting the admin to buy yet another point product or cloud service to solve this issue). Also, there still might be latency getting to applications etc., but now the admin has zero visibility, bringing us to our next issue…
- Lack of Visibility: If mobile users encounter broken connectivity, intermittent jitter, delay, packet loss, or overall slowness getting to one application but not another, or latency when accessing all applications then how and where do go to you triangulate the root cause? What if you want visibility into user traffic, the applications they are using, and the applications they are experiencing latency in? You also may want to identify why the latency is occurring, when it is happening, and the frequency of the reported latency.
- WAN Transformation: What if, during your WAN transformation, you want a guaranteed performance increase/uptime for users and applications? There is an increasing need to completely transform the Wide Area Network (WAN) due to expensive leased lines (MPLS specifically), while eliminating single points of failure and building in resiliency which was never there before, while safeguarding against application brownout where chatty bandwidth intensive applications can “starve” out the traffic from other applications. This causes jitter/delay/latency or even outages with little or NO visibility into the root cause, while possibly bonding WAN links together as one overlay while securing traffic as it moves between networks (“East-West”) at each branch and data center.
- Staying or Going: Most companies, especially since the pandemic, have branches with expiring equipment, expiring licenses, expensive maintenance/upkeep/rent/real estate, etc. Are there branches you can “sunset”? If so, you can save on the aforementioned costs. If so, you’ve also increased your mobile user headcount.
- Expanding and Contracting Mobile User Headcount: Wouldn’t it be easier to have one service that is architected to sustain an expanding and contracting headcount of on-prem users and mobile users?
- Sprawling Corporate Perimeters: Today, fewer people travel to the office five days a week. This means one thing: more mobile users and increased reliance on private or public SaaS (software as a service) applications. When your users are working on the road or from home, each office is still a perimeter. But, now, each user becomes a corporate perimeter (multiplied by the number of users) because each desktop (and each individual desktop data connection to the Internet and back to corporate) must be secured. You also have SaaS applications with data containing your personal or corporate intellectual property. This is your company’s “secret sauce” which is simply “out there” living within applications that you have no control over. Your network and perimeters are now sprawling out of control with no strategy to “herd all the cats” to get all your data secured via one service, while doing so with as little latency as possible. Regarding the SaaS applications, what if you want to know who that information is being shared with and where it has gone recently? Does it contain malware? Who has rights to access it via download, who can upload data, or who should not have rights to access this information? Every user and every application is a corporate perimeter. Never forget that the frontline is everywhere...literally everywhere your employees are.
- Global Connectivity: WHAT IF…on a GLOBAL basis, you want to interconnect all your mobile users/remote branches/data centers together while securing SaaS applications, while performing DLP for application traffic, while having visibility into all traffic traversing this service, WHILE doing all of this securely/preventing known malware and zero day malware with a product which is deployed GLOBALLY (so, wherever the user is, wherever the branch or data center is, the SASE service is local to YOU!), while managing this SASE service with one GUI?
Ask Yourself And Your Team The Tough Questions
- List out your current pain points about your network and network security. What keeps you up at night? What does the company really value and what is core to the business? What do you like and dislike about your current network and network security? What is preventing you from achieving your transformation and security goals?
- What does “ZTNA” mean to your organization? I defined ZTNA in my previous article, but what does it mean and how does it impact YOU?
- Does your organization have a consistent security posture which can be easily implemented for all users, all mobile users, all sites, all applications everywhere?
- Then, ask yourself: Why make changes based on your business initiatives? What is the technology gap you are faced with? How do those issues map to meet or miss business goals? What is your ideal business outcome and why solve it now? What is the risk of doing nothing vs. strengthening your network and security posture ASAP?
- Regarding the risk of doing nothing, always remember: an exploit (an attack sequence used by an attacker) targets a vulnerability (flaw in the software targeted by the attacker that, when targeted, produces a result intended by the attacker but unforeseen by the customer) to create a code execution (aka, deploy malware code and executables). What is your organization doing, right now, to prevent known and zero-day malware? And how do you know that it’s working? How do you even know whether or not you, your co-workers, or your entire organization has been breached? Typically, no one ever knows. If they do find out, it is typically a minimum of 60 days after the fact. Most breaches happen silently. Why would the attacker want to alert anyone? They don’t want to interrupt what they’re doing while they continually interrupt what you’re doing! Why let them leach off you for free? These people are on your payroll and you don’t even realize it. Fix the glitch!
- How can I proactively mitigate the inception and spread of zero day malware in real time at the “front door” so I can stop being reactive to the spread of malware?
- Are you drowning in log spam and have no way to figure out the alerts to focus on? Which alerts correlate together?
- Why are you considering one vendor vs. another and do they fully cover ZTNA 2.0? Do they fully mitigate zero-day malware?
- How many workers do you have worldwide? Including contractors, what is the projected number 3-5 years from now? Which geographic locations do they reside in? Where will they be in the future...traveling, perhaps? How many remote workers at peak times? Do workers need to “phone home” back to your company or do they access SaaS applications directly via the Internet? How is mobile user data kept safe while the user is at home or traveling?
- When a user is remote, is VPN enough security? How is a user and their device authenticated?
- Least Privilege Access and Continuous Trust Verification: Can I trust users (identity by User-ID and Group-ID) and devices to access specific applications and internal or Internet based corporate resources the entire time? Are users doing the right things while connected? How do you know? How do they know?
- How do you ensure that “X” group of users can only access “X” group of applications? Same question regarding contractor access to your organization! How do you police this?
- How many branches do you have, are all of them staying or going? Do you have legacy edge appliances at the Internet edge at the branches? How do you enforce security either way? How much bandwidth is needed at each branch? Do the branches need to access each other? How do branches access the data centers? Is that access sufficient or does it need improvement? Are you currently backhauling (user/branch) data connections and causing unnecessary latency? Are you prioritizing business critical and latency-sensitive application traffic?
- Can you perform micro-segmentation at the branch?
- Do remote workers need to access the branches and data centers, or just the data centers?
- How are you enforcing security when people and applications “scatter”? How do you know?
- How are you networking to and reaching applications in the Data Center/reaching Cloud or Internet applications?
- Most companies use SaaS applications. Which SaaS applications does your company use and rely on today? Is access to every application allowed for every user? Is access to all data in the application allowed for every user? Which applications are trusted and for which users/which applications are blocked for certain users and not others? Which applications are blocked for all users? Which applications are tolerated? How are applications used? How is the application set up and is it set up securely? Where is your data going? Is it being shared elsewhere? Does it contain malware? Do you know and do you have visibility into all of this? What about Data loss (leak) prevention? What about policy recommendations and compliance for applications and access to sensitive data?
- For Internet or cloud-based applications, do you have per-application/per-user visibility when things go wrong intermittently?
- Are you doing SSL/TLS decryption at scale without oversubscribing your resources?
- If you want to change your security and WAN architecture, can you implement this security quickly, everywhere, at hyper-scale, cost friendly, and without oversubscription?
- Lastly, remember: Most people feel that the product priced the lowest wins. This is exactly the wrong mentality when it comes to security. Think to yourself: what if the company gets breached? If so, the brand, the name, and the entire company is at risk and with it, all of our data is at risk. How much would you pay to secure your data, your intellectual property, the “secret sauce” of the products you sell? How much is all of that worth (hint: there’s no way to quantify this)? What keeps the owners of the company up at night? Does your current security solution keep pace with the threat landscape? The best idea is to buy a product that is scalable and mitigates zero day malware!
Real World Examples
Let’s consider two scenarios: (1) a legacy enterprise network without SASE and (2) that same network transformed with the power of SASE.
Legacy Network
Please see the network diagram below. This diagram is a composite of several real-life legacy networks observed over the years.
(click to enlarge)
This is a complicated diagram. Simplifying it, let’s go over what we see:
- Mobile Users: Several hundred or even several thousands of mobile users using desktops of various operating systems. While at home, the mobile users have insecure, unfettered access to the Internet. The mobile users use client VPN to connect back to the “Boston” site. They are dispersed throughout various geographic areas in North America (average latency to connect to Boston from Southern California: ~70-one00ms), several in Europe (average latency to connect to Boston: one00-200ms), Asia and India (average latency to connect to Boston: 300ms). Most mobile users are internal “trusted” employees. Some mobile users are external contractors. All users need to connect back to the “Boston” site (corporate HQ) and the “Penn” (data center) site to access resources, such as private applications, remote desktop sessions, etc. But, these connections are backhauled, causing latency. Mobile users are allowed to connect, trusted, allowed, then their traffic and connections are ignored by admins.
- Branches: Branch users connect to the Internet via their local ISP. Two branches have “next-gen firewalls” (UK, Pakistan). Several branches either connect to the Internet via routers or legacy firewalls (China, India, Africa, Brazil). All branches connect back to the Boston and Penn sites via expensive MPLS connections. The global MPLS contract expires in 8 months. The company is trying to decide whether or not to keep MPLS. Several branches will be going away soon. All users at those branches will become mobile users. Branches connect to each other via site to site VPN if MPLS is down. Certain branches have full legacy SD-WAN connectivity to each other if MPLS is down, but they do not have backup connections to other branches. All branches backhaul connections to Boston and Penn sites, causing latency.
- SaaS Applications: All users (mobile users, branch users, Boston users, Penn servers) connect to the Internet via their local ISP. Consequently, they connect to their public SaaS applications via their local ISP as well. Most of the company’s intellectual property is “housed” within these SAAS applications with no security and no visibility into who is accessing what.
- Is there next-gen L3 through L7 security? Very little in this environment.
Now, let’s briefly dive into the issues with this network:
- Many different types of WAN edge devices at each branch. This is a cobbled WAN with no consistent WAN backup link strategy. Admins manage each device one by one, causing inconsistent security policies and complications leading to human error. When branches reach other branches (moving East-West), they do so mostly without firewall enforcement, meaning that a malware outbreak will be allowed to happen.
- Branches and mobile users backhaul connections to Boston and Penn. This causes network-wide latency.
- Branch WAN edge devices do not have the capability to route applications over specific links or apply QOS (quality of service) or any other type of priority based on mission critical or latency sensitive applications
- Branches connect to each other via MPLS. MPLS is an expensive legacy WAN technology. Further, branches could be connecting to each other using both MPLS links and Internet links, bonding both links together. Thus, there are expensive WAN links and very little security.
- Mobile users are allowed to connect to any resource on the Internet, to any branch and to any SaaS application. This is “allow and ignore”. This is a security breach waiting to happen!
- Each branch, data center, HQ, user desktop is a perimeter. Perimeters expanding out of control. There is no inline security inspection.
- If there is intermittent latency when accessing a SAAS application, it can be impossible to triangulate the root cause due to lack of user and application visibility.
- There is a long overdue, dire need for WAN transformation and ubiquitous next-gen L3 through L7 security with SaaS Security and ZTNA 2.0
The Same Network Transformed With SASE
This is the same network as above transformed with SASE. Please see the network diagram below.
(click to enlarge)
- Site-to-site VPN and WAN Transformation with SD-WAN: Backhauling site-to-site traffic is eliminated completely as all site-to-site traffic traverses the SASE service. Combining multiple WAN “underlay” links (ex. Internet and MPLS links, secondary and tertiary Internet links) as primary and secondary “overlay” paths while prioritizing mission critical and latency sensitive applications. Eventually, admins can remove expensive WAN links, replacing them with more cost effective links. All site-to-site WAN traffic traverses the FWaaS feature of the SASE service, preventing East-West malware outbreaks
- Mobile User Transformation: Although mobile users are geographically dispersed, the SASE service is local to each user within their geographic region. This eliminates backhauling of mobile user connections (client VPN, clientless VPN, SDP, explicit proxy etc.) to a regional headquarters site. Mobile user desktops are posture checked to ensure that they are trusted devices with software updated to certain patch levels, etc. Mobile users are authenticated, via a central user database, then challenged with “two-factor” authentication. Mobile user traffic to branches/data centers/Internet traverses the FWaaS, keeping mobile user traffic secured. Mobile users are segmented such that certain user groups can access certain applications while other user groups can access other applications but not applications used by another user group, etc. Contractors only have access to certain applications.
- Cloud-Delivered Next-Gen Security as a Service with ZTNA 2.0 (Least Privilege Access, Continuous Trust Verification, Continuous Security Inspection, Protect all Data, Protect all Applications over any protocol): Zero-Day Malware Prevention/FWaaS/SWG/Explicit Proxy* (depends on the vendor, not a requirement for SASE but a “nice to have”/CASB/client and clientless VPN)
- Scalable SSL/TLS Decryption: for your environment, globally, without risk of oversubscription!
- Operational Efficacy, via One Management Console: Your environment GLOBALLY and Local everywhere. Elastic, scalable, redundant, and five 9s uptime.
- Visibility with DEM: To help organizations monitor and improve application and user experience with the ability to triage packet loss, jitter, delay and latency for each user accessing each application while traversing the SASE service by monitoring each application session, testing performance and collecting data to be used to triage issues
- SAAS Security with CASB and DLP: Protection of SaaS applications from cyber threats/application posture/identity based application security/data governance. Sanctioning certain applications. Blacklisting unsanctioned applications. Tolerating certain applications. Inspection for data at rest, data in motion (upload/download), remediation of misconfigured security settings in sanctioned applications via continuous monitoring. Detailed application use analytics and visibility. Enforcement of who gets access to what data. DLP (data loss prevention) to prevent intellectual property from being accessed by unauthorized users/data discovery/who owns the data and policy for that data, who will get in trouble if that data is leaked? How is the data classified?
Help is Here!
All these issues can be solved by one SASE service which can deliver features such as: Firewall as a Service (FWaaS) to secure mobile user traffic/branch to branch/branch to data center/branch to Internet/mobile user to branch/mobile user to data center/mobile user to Internet traffic/prevent known and unknown malware outbreaks, delivering SD-WAN for optimal application prioritization and WAN transformation, CASB and SAAS Security with DLP, visibility into all traffic traversing the SASE service with “DEM” (digital experience management monitoring). This product can replace many appliances and point products. The product can deliver ZTNA 2.0 and can be managed via one GUI as one cloud-delivered, scalable, global SASE service. Imagine, one perimeter to meet your security needs to help you transform your network, while helping to solve and prevent security issues on an environment-wide globally scalable basis!
SASE takes your network from technologies that worked well in the 1990’s, the 2000’s, the 2010’s and earlier in the 2020’s, then systematically layers features on top of the service to arrive at the ultimate goal of YOUR enterprise network security built within the ZTNA 2.0 framework. SASE is “Networking and Security 2.0”.
Always remember: With SASE, the goal is SECURITY and WAN transformation, not simply access or set it then forget it! Oftentimes, network and security engineers connect their users and environment to a SASE service, add a few firewall rules, then call it a day. This is exactly the WRONG thing to do. Establishing connectivity to a SASE service is only the first step in your journey to achieving ZTNA 2.0.
Worth reiterating: If you’ve only deployed the “Secure Access” part of SASE, you have begun. But, never forget that you are only at the ground floor as far as accomplishing the ultimate goal, which is to the secure that edge! Do mountaineers stop climbing once they reach Everest base camp? No, and protecting an enterprise network environment demands collective action and trust is a vulnerability. Once connectivity has been established to a SASE service, you must take advantage of the “Service Edge” functionality or you are not using the product to its full advantage to protect “DAAS” (data, assets, applications and services). Keeping going until you have consumed all of the features at the “Service Edge” layer of SASE that you need for your environment.
When protecting your environment, do NOT forget about SaaS Security and DLP. Do NOT “kick the can down the road” on this. If you are not securing users, applications and the data which users can access, you are NOT and never will be doing ZTNA 2.0. Use the features at your fingertips. They work! And, they will not cause interruptions when deployed properly.
If your organization has these challenges, your organization should consider SASE:
- Geographically dispersed mobile users/need strict authentication/need posture checks/“allow and ignore” stance toward user traffic but has a desire to move towards tight mobile user security
- Need for secure, yet limited contractor access
- Several branches, data centers and HQ locations, all geographically dispersed and Backhauling Traffic
- Business Growth (users and locations)! Or sporadic growth at times (elasticity!)
- Need to remove or combine usage of expensive WAN links, but also want to do East-West Security across a WAN = Need for WAN transformation with micro-segmentation at the branch
- Branch or office downsizing = increase in # of mobile users and need for app security!
- Any customer who does not have consistent Security Posture everywhere or have a Security Strategy
- Need to secure SaaS apps with Visibility into user and application traffic
- Any customer whose attack surface is expanding (expanding perimeter) and they do NOT have a handle on it!
- Striving towards a ZTNA 2.0 security posture
Do you need help in your journey to SASE, SaaS Security, WAN transformation, ZTNA 2.0 or any of the features mentioned in this blog? Please reach out to either myself or any of our cybersecurity experts. I am available on LinkedIn. Let’s meet in person for a conversation on how we can help. Thanks for reading!
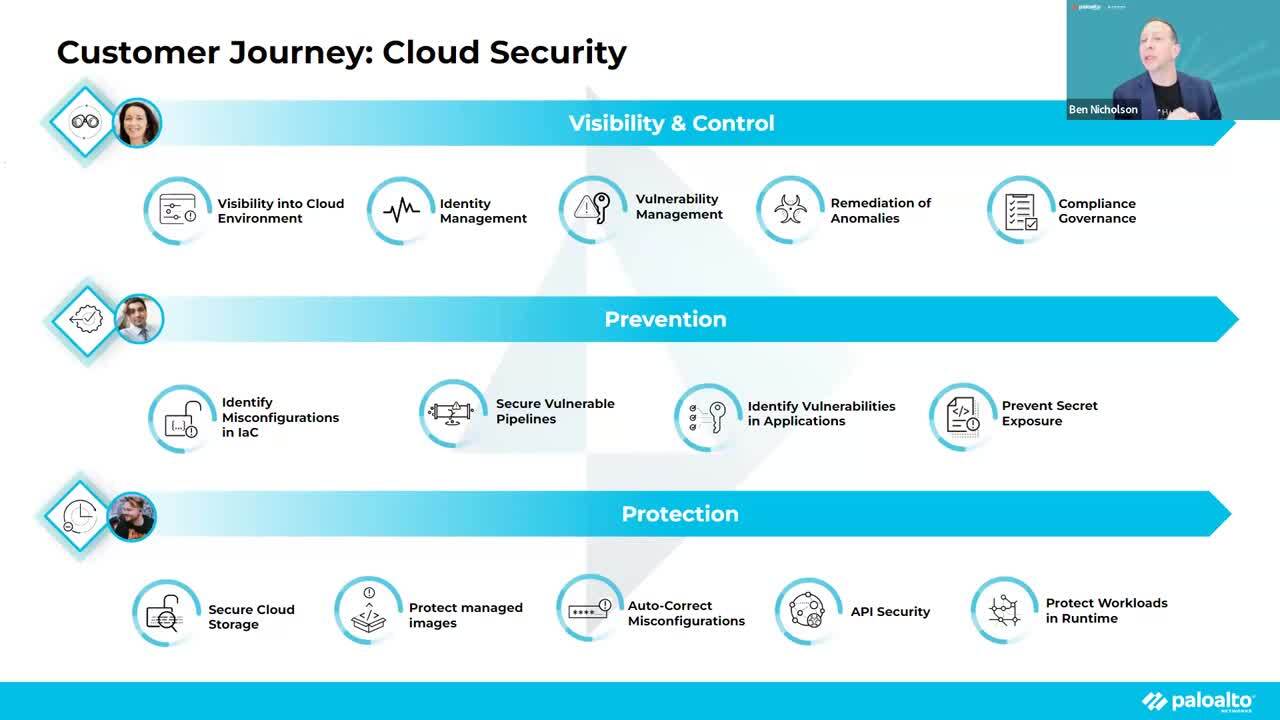
Next steps: Watch WEI's webinar focused on Prisma Cloud by Palo Alto Networks. Ben Nicholson reviews Prisma Cloud's capabilities in attack path analysis, identifying the source of risk, attack surface management, and much more. View the full webinar below!
Webinar: Cloud App Protection Using Code To Cloud Intelligence With Prisma Cloud